tldr: Don’t click on that link unless you’re really sure, and if you do take precautions.
I hate spam as much as the next person, but for those of us in customer-facing tech roles the worst kind of spam is the clever kind.
Most of us know not to click on the promise from the Nigerian Prince, but unfortunately the level of creativity some scammers show would be enviable if they actually dedicated their efforts to something worthwhile.
Today I received this fairly harmless looking contact form submission. I thought I would use this as an example for others to help weed out some of the scammers and hopefully save someone somewhere some future heartache!
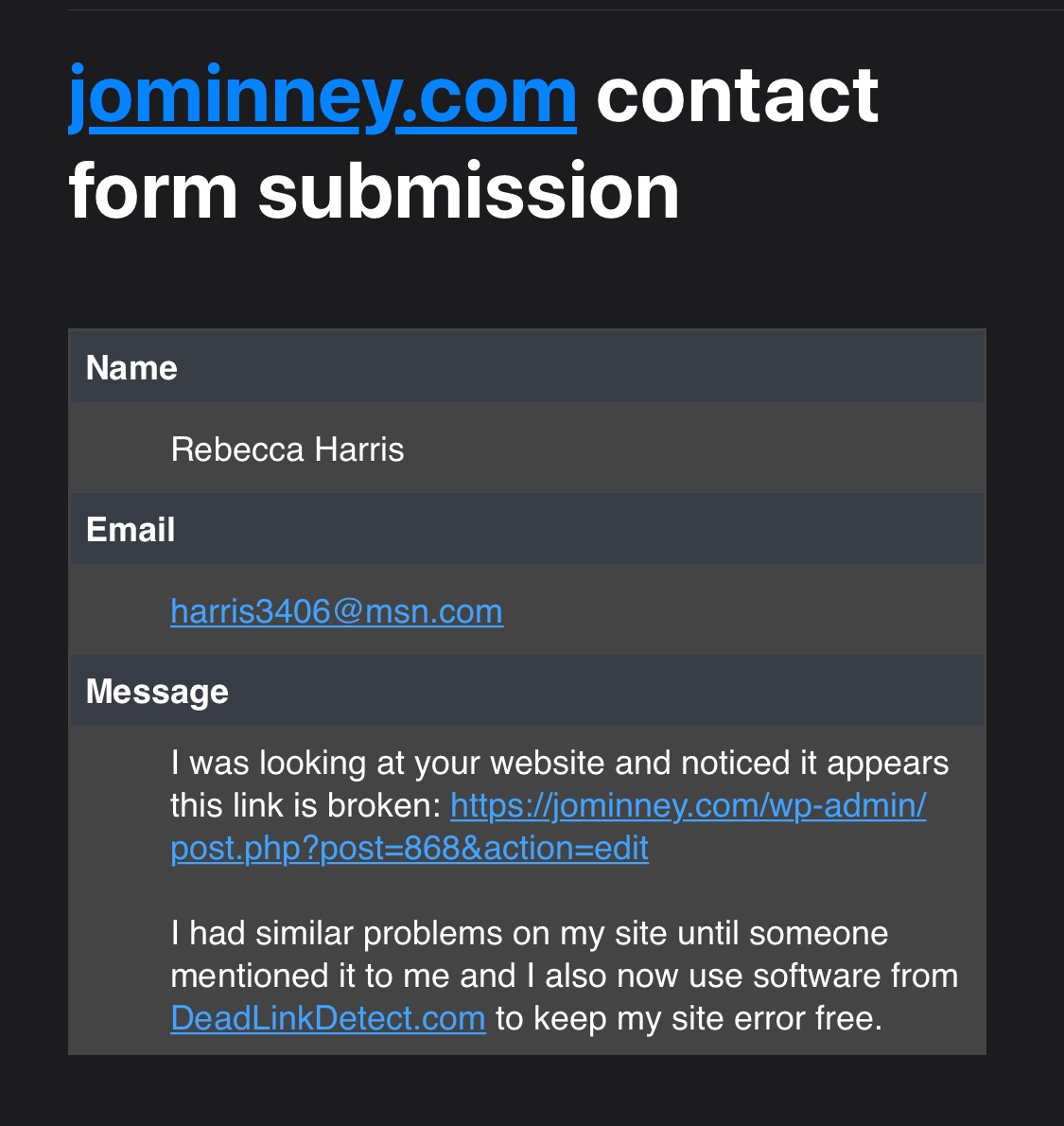
You might look at this and think “obviously it’s spam but it’s pretty harmless, what’s the big deal?”
Let’s break it down…
1. Name
One of the oldest tricks in the book, the sender has used a common Western name that wouldn’t raise any red flags. I have both clients named Rebecca, and clients with the surname “Harris” both of which are common in Australia.
2. Email
I’m giving them a 7/10 for effort here, because they went with msn.com instead of the more commonly used gmail.com, but I’ll let it slide because they still put a decent amount of thought into it. Instead of random gibberish or an unrelated name, they used the alleged surname of our esteemed “sender” so at a glance it passes the second test.
3. Message
Let’s break it down a bit!
a) Language
It’s in plain English with a conversational tone. Not the best grammar but certainly no worse than the majority of people I communicate with via email on a daily basis. There are no obvious spelling errors and it is written in the first person (I was, I had) with nicely spaced paragraphs for easy reading. 10/10 here.
b) Content
While I immediately identified this as spam, I also know that a huge number of clients I’ve helped through the Digital Solutions program would not have noticed the red flags! Let’s start with the first paragraph…
I was looking at your website and noticed it appears this link is broken: [dodgy link goes here]
– Allegedly Rebecca Harris
The link in question was actually a legitimate link – if I’m logged in. As someone who works intimately with WordPress, I already know this, but unfortunately for a lot of my clients that is not the case.
For readers who aren’t aware, any URL that includes the string of text “/wp-admin/” is typically only visible to users who are logged in to a WordPress site. Depending on the level of security you have set up on your website, this may either take you to a 404 page or prompt you to log in to your site if you aren’t already. If you are logged in, it will likely direct you to the WordPress dashboard to edit the post in question.
In this particular case, I am pretty sure that the sender is trying to take advantage of the lack of understanding of many WordPress users to convince them that a particular link is either broken or accessible when it shouldn’t be, so that they will pay attention to the email. However, this technique is also commonly used to convince WordPress administrators to log in to their websites so that they will click on questionable links from within the dashboard that will potentially have disastrous effects!
I’ll admit, I’m no hacker. However, Stephen Rees-Carter (former Senior Developer at WordFence and certified ethical hacker, definitely is. In a fantastic live demo at WordCamp Brisbane 2019 it was my pleasure to introduce Stephen’s presentation titled ‘Think Like a Hacker’ where he live hacked a WordPress installation in a bunch of different ways live on stage.
The one that really struck me as SCARY was the use of hyperlinks in comments that, when followed while logged in, allowed the malicious actor to conduct actions on the target site including the upload of executable code that could do pretty much anything. Imagine this scenario for a second:
You write a blog post. Someone with a normal seeming name leaves a comment:
Great blog post, thanks for sharing! I gave you a shout out in my recent article here. Keep up the good work 🙂
– Jessica Ramble
Now, like all good blog owners, you log on to your website when you receive comments or notifications to investigate them. You see this totally legitimate and normal looking comment, and click on the link to view the article you’ve been featured in. How exciting! Unfortunately, it looks like the commenter has made a mistake in the link, and it just goes to a 404 page. You close the tab, and think nothing of it. Unbeknownst to you, clicking on that link while logged in to your dashboard has just given ‘Jessica Ramble’ administrator access to your website!
When I received the contact form submission that spurred me to write this blog post, I reached out to Stephen to see if he had anything to add.
This comment reeks of a social engineering attack designed to trick the victim into believing something bad is happening, so they’ll do what you’re asking them to do.
It’s the same technique that many phone scammers use, the ones claiming to come form “Microsoft Support” or “Apple Support”. They get the victim to open up some innocent system app, such as the event viewer on Windows, and then look for “errors” in the output (i.e. normal log entries which can be safely ignored). Once the victim finds an “error”, they stress how that’s a sign they’ve been hacked and get the victim to either sign up for their “cleaning service” or install remote desktop control software, and then come back later to compromise the computer or steal data.
The other option here could be a much more targeted attack: if the victim clicks the first link, it would encourage them to log in to WordPress. Once logged in, they would then visit the site the attacker controls – which can then attempt a Cross-Site Request Forgery (CSRF) attack on WordPress. This attack relies on the victim being logged into WordPress (which they just did), and a CSRF vulnerability on the site. In such a scenario, the attack would have full access over the site within minutes.
Either way, this comment should be treated carefully. My advice, if you want to open their link at all, is to open it in a Incognito Browser window – safely separated from your WordPress site. But you should probably just delete it without clicking either link.
Stephen Rees-Carter, Ethical Hacker
I’ve bolded the most important bit, because if you take nothing away from reading this other than that, I feel like it was worth the time it took me to write it. I was reading a thread about Cybersecurity on Twitter the other day, and saw the best comment on a thread about describing cybersecurity to non-technical people. It was something like:
I protect digital assets from humans. Also sometimes, computers.
For the life of me I couldn’t find it again, but it is pretty accurate – the biggest cybersecurity threat is users. The best way to protect against it is to educate yourself, your friends, your family, and your colleagues. It doesn’t matter how many security measures you put in place – if you give your login credentials to someone they can still hack you.
To summarise, here’s a cat video:

